
Cyber Strategy
Why we need to make the effort
In today's interconnected world, where digital technology permeates every aspect of business operations, cybersecurity has become an indispensable aspect of any successful enterprise. While large corporations often have dedicated cybersecurity teams and extensive resources, small businesses may feel overwhelmed by the complexities of protecting their digital assets. However, neglecting cybersecurity is akin to leaving your front door unlocked, inviting potential intruders to steal valuable information, disrupt operations, and damage your reputation.
Small businesses may think they're not a target for cyber criminals, but that's not the case. Hackers often target smaller businesses because they believe they're less likely to have strong security measures in place. A cyber-attack can have a ripple effect, causing financial loss, reputation damage, and operational disruption.
Why a Cyber security Strategy is Key
A cyber security strategy is a comprehensive plan that outlines your business's approach to protecting its data and systems from cyber-attacks. It should identify your specific risks, prioritise your security needs, and outline the steps you will take to mitigate those risks. Throughout this series of articles, we will guide you through implementing a cyber security strategy so you can significantly reduce your risk of cyber-attacks and protect your business from the devastating consequences.
Fortunately, there are several organizations and governing bodies that provide guides on how to set up a cyber strategy. We will introduce these and go through the basic steps to creating your own unique program for your business.
Welcome to NIST Cyber Security Framework
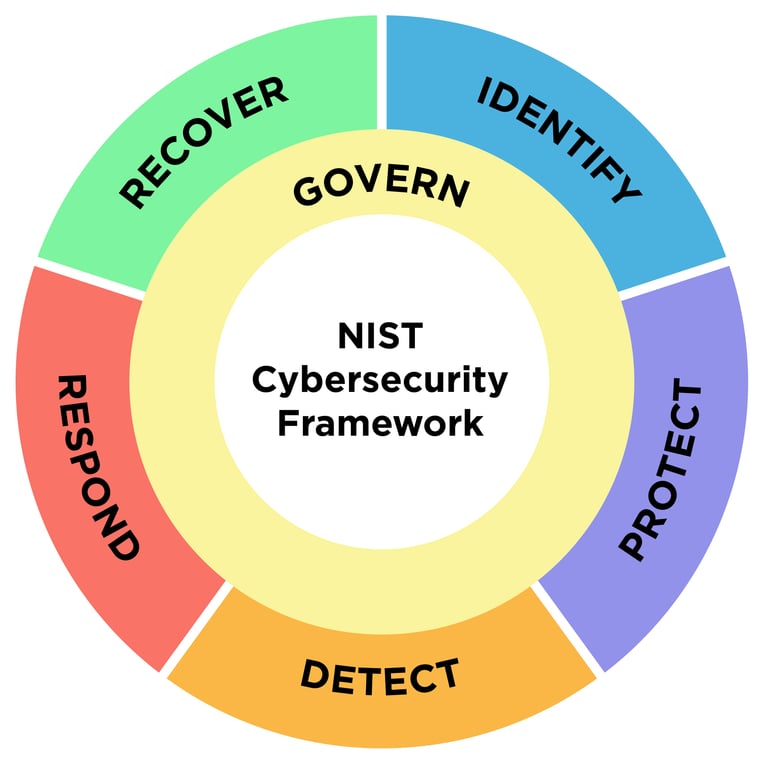
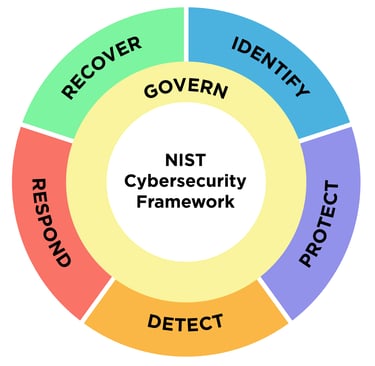
Our main guide will be the NIST Cybersecurity Framework, which is a set of guidelines for mitigating organizational cybersecurity risks, published by the US National Institute of Standards and Technology based on existing standards, guidelines, and practices.
We have chosen this because it is freely available and used by many countries as its preferred cyber framework. Version 2, whilst it is still in draft, is close to release and will be our basis, however we will be using content from many different agencies and governments.


Embracing Cybersecurity for Small Businesses
Keep Moving Forward
Cybersecurity is not a one-time project; it's an ongoing process that requires continuous vigilance and adaptation. As technology evolves and threats change, your cybersecurity measures should evolve alongside them. Regularly assess your security posture, identify gaps, and implement necessary updates to maintain a robust defense.
Remember, cybersecurity is not about preventing every attack; it's about reducing your risk profile, minimizing potential damage, and minimizing downtime.
By investing in basic cybersecurity practices and seeking professional guidance when needed, you can safeguard your business from the ever-present threat of cybercrime.
After going through our articles, you may then wish to move forward and mature the processes by achieving formal certifications such as ISO or UK Cyber Essentials. These are a great way to show your clients or partners that your business is equipped to manage their data or processes and will help you stand out from competitors.
Identify: Develop an organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.
Protect: Develop and implement the appropriate safeguards to ensure delivery of services.
Detect: Develop and implement the appropriate activities to identify the occurrence of a cybersecurity event.
Respond: Develop and implement the appropriate activities to take action regarding a detected cybersecurity event.
Recover: Develop and implement the appropriate activities to maintain plans for resilience and to restore any capabilities or services that we impaired due to a cybersecurity event.
Govern: Develop and monitor the organizations cybersecurity risk management strategy, expectations and policy.